As the backbone of many modern enterprise applications, XML Web Services play a crucial role in enabling communication between different software systems. These services, which often rely on XML (Extensible Markup Language) as a data format, use standardized protocols such as SOAP (Simple Object Access Protocol) and WSDL (Web Services Description Language) to facilitate interactions between applications across the internet. From financial institutions to e-commerce platforms, XML Web Services are integral in connecting various systems and exchanging critical information.
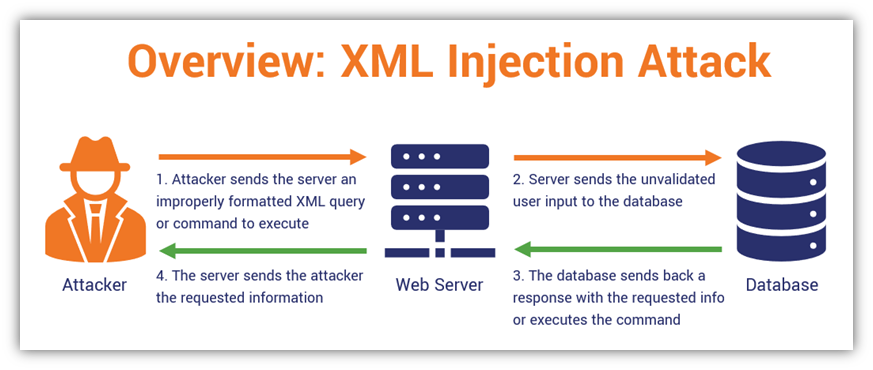
However, with this widespread adoption comes a growing array of security concerns. Just as XML Web Services provide numerous benefits—such as flexibility, interoperability, and platform independence—they also introduce a variety of potential vulnerabilities. The structured nature of XML, while advantageous for processing and communication, opens the door to complex attacks that target the underlying services. These attacks can range from XML External Entity (XXE) injections, which allow attackers to access sensitive files, to SOAP Injection, where attackers manipulate web service requests to execute malicious commands.
The complexity of XML-based services makes them a prime target for cybercriminals, who exploit weaknesses in how these services handle incoming data. Inadequate input validation, improper configuration of XML parsers, and poor security measures often create entry points for attackers. For instance, one of the most prevalent issues—XXE attacks—takes advantage of weak XML parsers to exploit external entities, allowing attackers to steal sensitive information or even gain remote control over affected systems.
SOAP Injection
is another common attack vector, where malicious data is injected into SOAP requests, bypassing security controls and enabling unauthorized access or modification of data. In extreme cases, these vulnerabilities can lead to the full compromise of critical business systems, resulting in severe financial and reputational damage. The Denial of Service (DoS) attack, targeting the service’s ability to function by overwhelming it with oversized XML payloads or recursive entities, is yet another way attackers can exploit XML Web Services.
Despite these risks, the importance of XML Web Services in modern IT infrastructure means that eliminating them is not an option. Instead, businesses must adopt robust security measures to defend against these attacks. Implementing strong input validation, disabling external entity parsing, and enforcing secure coding practices are just a few of the steps necessary to protect XML Web Services from exploitation.
This blog will delve into the intricacies of Attacking XML Web Services, exploring the most common vulnerabilities, providing real-world examples of successful attacks, and offering detailed guidance on how to defend against them. We’ll also look at the latest trends in security for XML Web Services and discuss how businesses can stay ahead of the curve to prevent these attacks from compromising their systems. By understanding the nature of these vulnerabilities and how attackers exploit them, organizations can take proactive steps to secure their web services and protect sensitive data.
As you read through this blog, you’ll gain insights into the various attack vectors used to compromise XML Web Services, from XXE attacks to SOAP Injection and Denial-of-Service attacks. We'll also explore practical solutions and security best practices that can help organizations defend their systems and prevent attackers from exploiting these vulnerabilities.
In the modern digital landscape, where data is increasingly valuable and systems are more interconnected than ever, ensuring the security of XML Web Services is paramount. Let’s dive deeper into how these services work, the specific vulnerabilities they face, and what can be done to mitigate these risks.
YouTube Video: XML Web Services Attack Demo
Below is a video demonstrating a SOAP Injection Attack using a popular web security tool. Watch the video to understand how these vulnerabilities can be exploited and how security mechanisms can be bypassed by attackers.
Resources
Here are some valuable resources that you can use to further your understanding of XML Web Services security:
OWASP XML External Entity (XXE) Prevention Cheat Sheet:
This cheat sheet provides comprehensive guidance on how to prevent XXE vulnerabilities in XML parsers.https://cheatsheetseries.owasp.org/cheatsheets/XML_External_Entity_Prevention_Cheat_Sheet.html
Web Services Attacks - Burp Suite Guide:
A practical guide on how to use Burp Suite to identify and exploit vulnerabilities in XML Web Services.
Comments
Post a Comment